This Session Hijacking Using Hamster and Ferret is another side of session hijacking. Previously I have already write how to do session hijacking in my other page about Firesheep HTTP Session Hijacking Tools that tools running on Mac OS.X and Windows Environment. Below I will use Hamster sidejacking in Linux. Hamster also available in Windows as a binary.
mediafire.com
2. Download, extract and build your hamster.
Go to hamster/build/gcc4/ folder and run make command(see picture below).
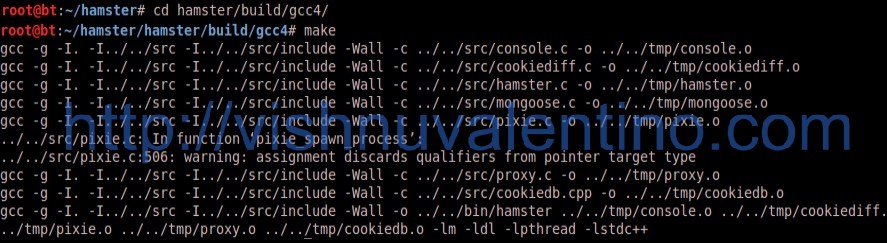
In your bin folder there should be a new hamster application.
Now, you also need to build your ferret(if you using Backtrack 5 R1 it’s already inside /pentest/sniffers/hamster/).
Go to ferret/build/gcc4/ folder and run make command(do the same with above step). In your bin folder there should be a new ferret application.
Copy your ferret and put together with hamster(see picture below).

That’s it how to build your hamster and ferret, now we will continue to the next step to set up the application to do sidejacking.
3. Hamster also work in wireless interface so you can choose which interface you will capture.
4. Running Hamster with command ./hamster on the terminal where Hamster located.
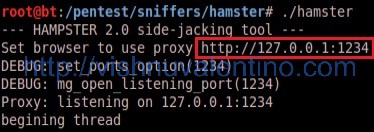
5. Open your browser and open http://127.0.0.1:1234.
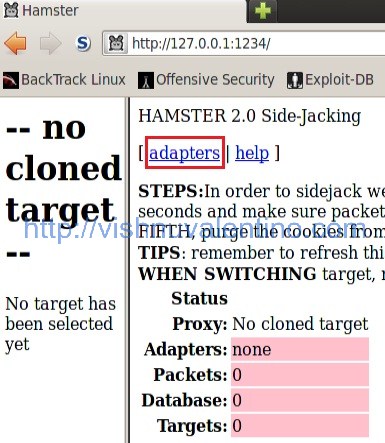
6. This is how Hamster looks like and you need to configure the network adapter. Click the adapter menu to choose network adapter.
7. In this page you should determine which adapter you will use to sniff the network. You can use ifconfig command to know your network adapter (example : wlan0 –> for wireless).
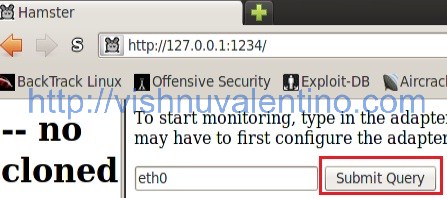
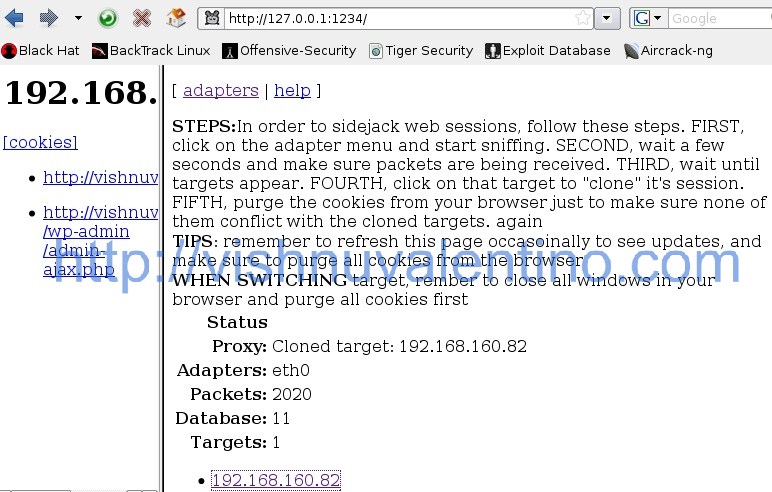
8. After you submit the query, now Ferret working in the background and capturing every cookie that pass the network adapter. When it’s success, just click the link on the left side to view the page as others.
That’s it. I hope you can use these tutorials in a good way 🙂 if any question, you can contact me or drop some comment.
 |
| hacking using hamster |
HTTP Session Hijacking
HTTP session hijacking is where the hacker grabs your “session cookies”. Your session with the web server is identified with a unique cookie. This cookie is sent to your browser at the start of the session, and your browser echos it back from that point forward.Ferret
This tools use to grab session cookies, running in the background process to capturing session cookies that pass the network at port 80.Hamster
This tools work as a proxy server to manipulate every data that has been grabbed by Ferret.Todo
1. You need to download Hamster.mediafire.com
2. Download, extract and build your hamster.
Go to hamster/build/gcc4/ folder and run make command(see picture below).

In your bin folder there should be a new hamster application.
Now, you also need to build your ferret(if you using Backtrack 5 R1 it’s already inside /pentest/sniffers/hamster/).
Go to ferret/build/gcc4/ folder and run make command(do the same with above step). In your bin folder there should be a new ferret application.
Copy your ferret and put together with hamster(see picture below).

That’s it how to build your hamster and ferret, now we will continue to the next step to set up the application to do sidejacking.
3. Hamster also work in wireless interface so you can choose which interface you will capture.
4. Running Hamster with command ./hamster on the terminal where Hamster located.

5. Open your browser and open http://127.0.0.1:1234.

6. This is how Hamster looks like and you need to configure the network adapter. Click the adapter menu to choose network adapter.
7. In this page you should determine which adapter you will use to sniff the network. You can use ifconfig command to know your network adapter (example : wlan0 –> for wireless).

8. After you submit the query, now Ferret working in the background and capturing every cookie that pass the network adapter. When it’s success, just click the link on the left side to view the page as others.

That’s it. I hope you can use these tutorials in a good way 🙂 if any question, you can contact me or drop some comment.


